Summary
You want show or use values from your own extended classes in SCOM with powershell?
Yes you can, this is possible with the following powershell commands.
Description
First you must declare your extended class. In my scenario I take the SCOM class “Windows Computer”. The new extended class are named “Windows Computer Extended Attributes”. Now, I filled up the extended class with a lot of data from monitored Windows and Linux computers. As example; Server function, server type, server team membership and a lot of other important data from registry and WMI. You can now filter, sort and group the monitored objects dynamically in SCOM with the data from the extended class.
Also, you can get the values with powershell and create some other great scripts.
The powershell commands
To get the SCOM class instance (extended class) you must declare first the extended SCOM class.
$Class = Get-SCOMClass | WHERE {$_.Displayname -eq "Windows Computer Extended Attribute"}
Now you can get the SCOM class instance (extended class). The command “Get-SCOMClassInstance” shows a large amount of data. I restrict the result with a monitored object, in this case I take a monitored Windows server. The Displayname must match exactly the Displayname from the monitored object, in my case the FQDN “hostname.domain.com”.
$SCOMExAttr = Get-SCOMClassInstance -Class $Class | WHERE {$_.Displayname -eq "srv11111.domain.com"}
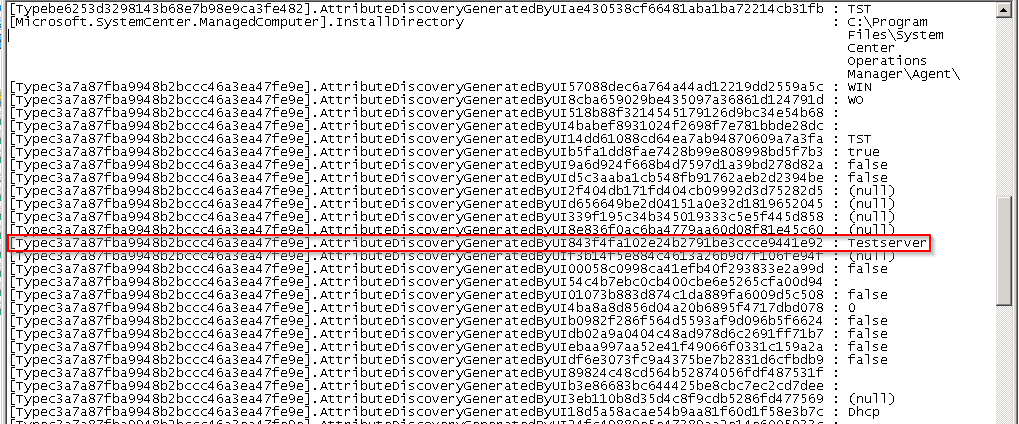
To figure out the value names to be used, you can export the SCOM class instance to a text file or something else.
$SCOMExAttr = Get-SCOMClassInstance -Class $Class | WHERE {$_.Displayname -eq "srv11111.domain.com"} | Format-List * >>C:\temp\srv11111.domain.com.txt
In the exported List, you can find the values that you need. You can see default values from the base class that you extended and the own values (imported attributes).
The following value names are relevant to continue with the powershell script. The value names in your own extended class have for all monitored objects the same UID.
- Server function:
[Typec3a7a87fba9948b2bccc46a3ea47fe9e].AttributeDiscoveryGeneratedByUI843f4fa102e24b2791be3ccce9441e92 - Server type:
[Type1a1021e9c2c6410dace6e73c3f95cb66].AttributeDiscoveryGeneratedByUIc16fe093d54846159a5f620545143277 - Active Directory Site:
[Microsoft.Windows.Computer].ActiveDirectorySite
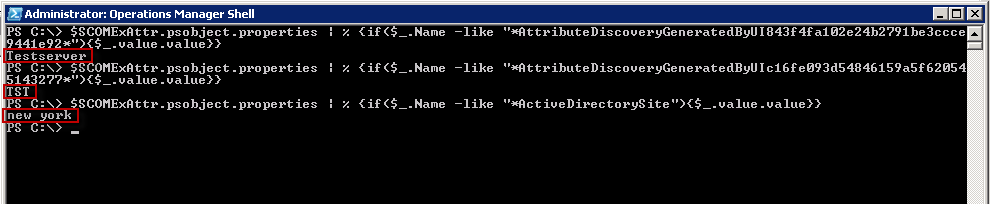
To get the values use the subsequent powershell command
1 2 3 | $SCOMExAttr.psobject.properties | % {if($_.Name -like "*AttributeDiscoveryGeneratedByUI843f4fa102e24b2791be3ccce9441e92*"){$_.value.value}} $SCOMExAttr.psobject.properties | % {if($_.Name -like "*AttributeDiscoveryGeneratedByUIc16fe093d54846159a5f620545143277*"){$_.value.value}} $SCOMExAttr.psobject.properties | % {if($_.Name -like "*ActiveDirectorySite"){$_.value.value}} |
Result
The script displays the following output. You can use this output to fill the custom fields from SCOM alerts and create some custom notifications.